No, the padlock next to your address bar doesn't mean a site is "reliable."

I regularly see this message on shopping sites, and I see that confusion is often made about what a secure connection is.
Securing the exchange with the web server
The presence of a lock near the address bar means that this site is using a TLS certificate to exchange data with you. This ensures that the data exchanged with you is encrypted. The primary purpose of a TLS certificate is to prevent "man in the middle" attacks.
In this type of scheme, a hacker intercepts the traffic before sending it back to the real target. If the exchange is done in an encrypted way, the content is not exploitable, because the hacker does not have the private key of the server, which is used to decrypt the content.
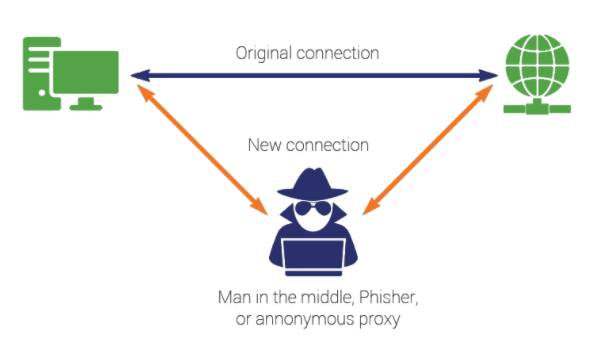
Because yes, the principle of "https" connections is based on an asymmetric key exchange, similar to that of SSL.
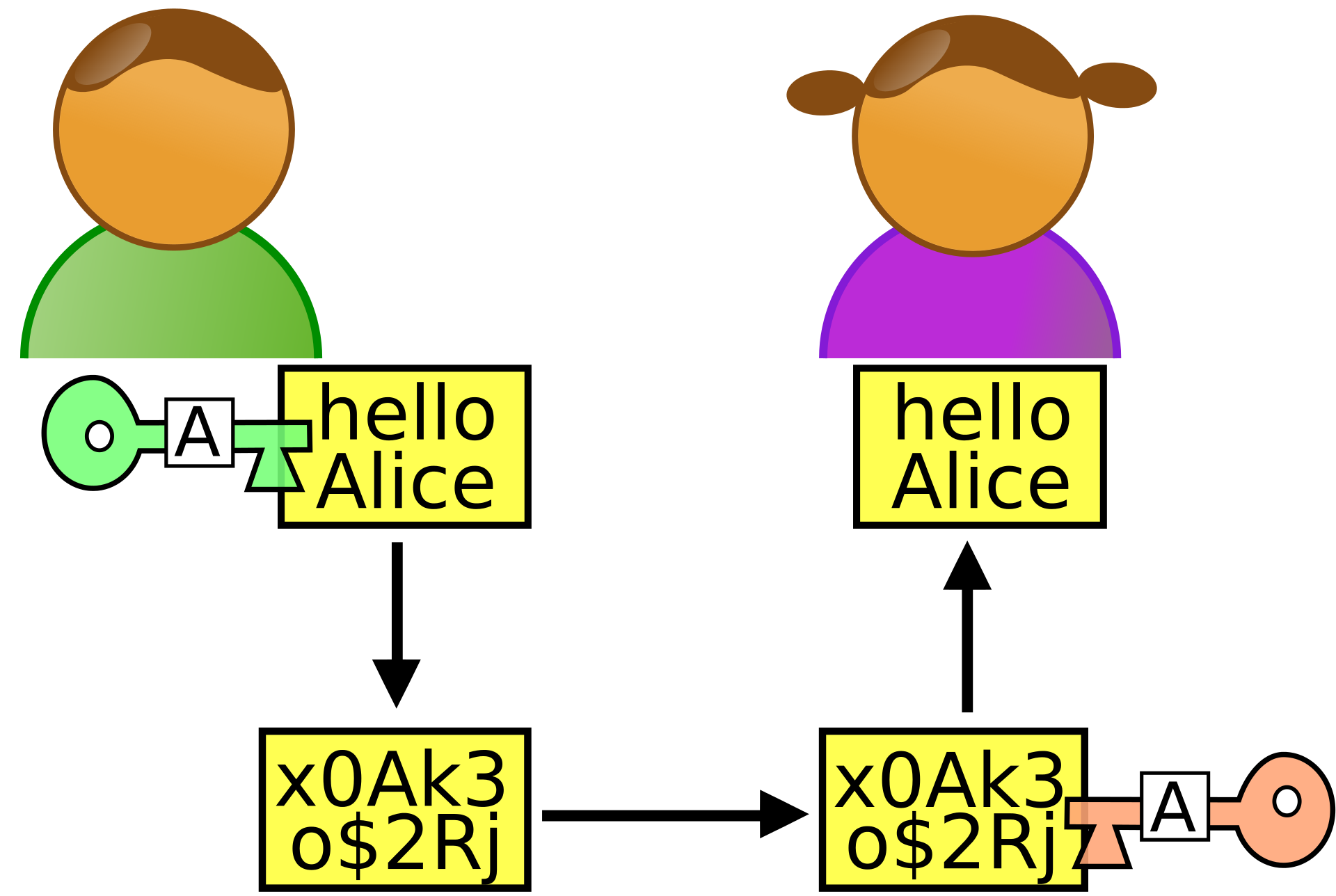
In this diagram, Bob (in green), knows Alice's public key, which he uses to encrypt her message. When he receives it, Alice uses her private key to decrypt the message. However, during transport, the message is not in clear text.
The other usefulness of a TLS certificate is that it is checked by your browser with certification authorities, which are there to validate that the certificate is authentic, and therefore that the site you are on is the real site. Nevertheless, as we will see below, it is possible to bypass this security as well.
Obtaining a TLS certificate, a matter of seconds
Until a few years ago, most of the sites using TLS certificates were corporate sites, because a TLS certificate costs several hundred or even several thousand euros per year. This point was prohibitive for a private individual, like me, who would have wanted to use a certificate to secure exchanges with his site.
Today, it is possible to obtain a valid certificate very quickly via some certification authorities such as Let's Encrypt, and all this for free! This is the solution used on this site.
That's why while a few years ago, the presence of a TLS certificate was reserved for professional sites, and not much used in the scam/phishing field, they are now present on 90% of them. The concern is that by repeating, wrongly, that the presence of the sacrosanct padlock means that the site is reliable, the user who is not aware of security is less vigilant.
Third party certification authorities and breach of protocol
Very fashionable a few years ago, some malware deployed third party certificate authorities on your workstation to validate fake certificates. Today, this is no longer really necessary, thanks (because of?) free authorities like let's encrypt.
This solution is often used in companies in the case of some https proxies, which pose as a certification authority to be able to intercept traffic.
As I said above, the presence of a TLS certificate means that your exchange to the web server is encrypted, which is a very good thing. Be careful though, it does not mean that the whole chain behind the server is also encrypted. Breaking the protocol is something common in companies, because certificate management can sometimes be complex. Moreover, it is very often considered that some network zones are considered "trusted zones", in which the interception of data would be complex, and moreover it is often about the exchange of non-sensitive information, not necessarily requiring the use of encryption.
DNS Spoofing/DNS cache poisoning
A fashionable attack in recent years, DNS Spoofing (or DNS cache poisoning) consists of compromising a DNS cache to send the user to another backend without him noticing because the URI in his address bar has not changed. The complete operation is described in a simple way on the CLoudFlare blog. In such cases, the presence of an extra TLS certificate requires the implementation of a third party authority, as described above. And the second part of the use of the certificate then makes sense.
It should be noted that some antivirus software can detect abnormal behaviour, and is able to determine some potential spoofing.
In conclusion
Sites that indicate that the TLS connection means the site is trustworthy play into the hands of scammers, as they allow the site to be considered authentic and trustworthy by users who are not security conscious.
A TLS certificate makes it possible to secure the exchange with the site, which makes it possible, for example, to exchange bank codes while greatly limiting the risk of interception. For my part, I automatically ban all sites that do not do TLS, which still exists in 2019!
A TLS certificate also guarantees that the site you have posted is the site corresponding to the certificate.
Nevertheless, a TLS certificate is not a panacea, its presence does not mean that the site is reliable! To do so, it is possible to check the reliability of a site via dedicated engines and be wary of details that would seem strange to you.
Moreover, using an antivirus with a heuristic engine (BitDefender or Kaspersky, to name but a few) is a significant plus.



Comments ()