Being a hacker isn't like being in the movies!

Hackers … we often see them in movies and TV shows. These experts are able to hijack NSA satellites with a string and a nail clipper (#MacGyver)! (Cover image from the movie Die hard 4)
I decided today to tell you about hacking in "real life". I consider myself to be a white hat (an ethical hacker) and I’m going to tell you about the common methods a hacker uses. I will focus here on the simplest part: websites.
Spoiler alert: you may be disappointed, many methods are very simple.
Important warning
The purpose of this post is not to promote hacking, but to demystify it and show a little bit what hacking is in real life. Don't get into hacking without knowing what you're doing and without taking the necessary precautions.
Hacking is considered a misdemeanor or a crime depending on the country. For information, in France, "Article 323-1 of the penal code punishes "the fact of accessing or remaining fraudulently, in all or part of an automated processing system". The penalty incurred is 2 years imprisonment and a €30,000 fine. This can be increased to 3 years imprisonment and a 45000€ fine when it results in "either the deletion or modification of data contained in the system, or an alteration of the functioning of this system".
Hack, what for?
Before talking about method and vector of attack, the right question is why hack?
To answer this question, there are, from my point of view, 2 sides of the same coin to consider, both types of hackers.
The white hat will try to find a loophole to signal it. Yes, but why report it?
- By conviction, personally I have already found major security holes by altruism, I’m in favor of a safer web for everyone.
- Because he participates in bounty bugs and will therefore receive a reward for reporting flaw (subject to certain criteria, such as non-disclosure within x days)
- By challenge, I am also in this case, the challenge to break, to bypass the security. The pleasure of solving puzzles more or less complex…
The black hat, on the other hand, will try to take advantage of his loophole. There are several solutions for that:
- Extract information and resell it on the black market. For example, an enriched contact (email address, password, phone number, first and last name) can sell for a few cents. Taking into account that many sites have thousands or even millions of contacts in their database, the price rises quickly.
- Selling confidential information or trade secrets
- Sell credit card/PayPal information, and so on…
- Making a site unavailable. Some offer DDOS "as a service", allowing for example to temporarily shut down a competitor to discredit it.
- Requesting ransom after encrypting all the data of a company or individual
- Turn the machine into a zombie, used in a botnet or for phishing emails.
The purpose of this article is not to be exhaustive, but to tell you the main reasons.
Observe to break better

We often talk about incredible hacks, but we often forget to talk about more basic hacks. I had the opportunity to get past the security of some websites simply by being an observer. For example, recently I managed to access very sensitive data on a website simply because of a display problem.
Indeed, one of the images had loaded badly, and I had the reflex of the good old CTRL+U (Display Source)!
What was not my surprise when I saw PHP errors, whose HTML rendering had been hidden… Then by going back to those errors, I discovered a debug module enabled on this production environment.
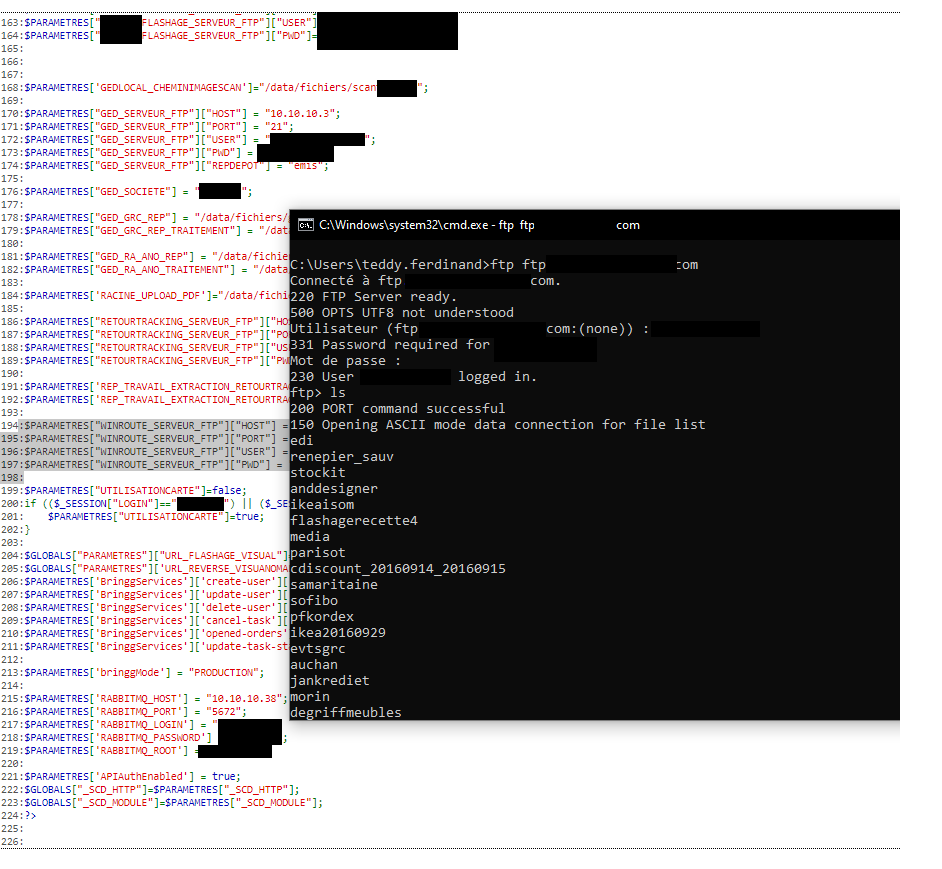
Via this debug module, I was able to trace the site configuration files, in which there were database connection strings, FTP server connection information and many other information, including confidential information.
This is just an example, but be aware that there are many such cases. Observing the source code or the behavior of a site gives clues on how to tamper with its operation. It is also possible to observe the behavior of the application using the development tools (F12). This makes it possible to observe XHR-type calls, which often correspond to API calls, when the latter are not sufficiently protected. It is sometimes possible to have them display data from other clients or information that is supposed to be protected.
In one of my previous missions, I had put my finger on a security anomaly of this type, by modifying an API call, I was able to access all the information of all the clients registered in the database (we were talking about several million clients in this case). Fortunately, I had identified this bug on a pre-production environment, and the bug was fixed before going into production.
A lot of hacking is in fact done by opportunism, simply because a flaw was visible. Surface attack remains the most common method!
Knowledge is power

Observing is good, knowing is just as useful. To know is to know several things:
- Knowing the target: being able to identify the CMS used, for example, or the type of server that runs the site.
- Know the common flaws
- Some common attack vectors: XHR, SQL Injection, etc.
Why is this important? As a demonstration, if I want to try to brute force a site, knowing if I'm on a WordPress or Drupal type CMS changes a lot, I'm not going to attack both in the same way.
Moreover, I'm going to try to look for the latest security patches to attack what they fix. In production, it is common for servers not to be updated as soon as a patch is released (except for big security patches announced by the editor beforehand).
In the same way, knowing that a server is running on an obsolete version of Apache HTTPD (for example once again) allows me to know how I can compromise it to potentially take control of it.
In the world of hacking, technology watch is essential. You need to keep up to date with the latest major vulnerabilities, the latest methods, and the most common techniques.
For example, Amazon recently suffered an attack of several Tb per second. Everyone has been focusing on volume, yet on the scale of AWS, it's a grain of sand. What is interesting is to understand the attack vector: the UDP reflecting. Indeed, knowing how someone generated such a bandwidth is much more useful than a "clickbait" volume.
The right tool for the right attack
Of course I will not expose here all the tools to make an attack, that's not the point, I will just talk about common tools that can be used quite easily.
Detection of CMS/solutions used
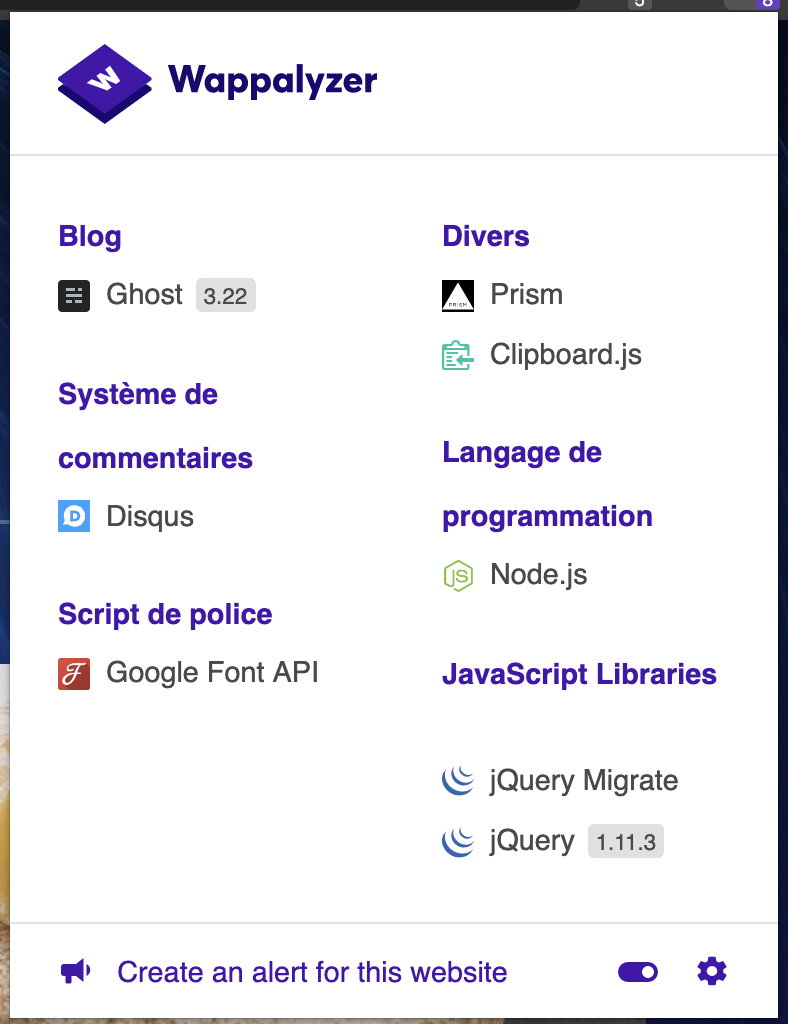
I'd already be talking about the Wappalyzer extension. This browser extension allows you to have a lot of information at a glance, simply based on the headers and the presence of certain key files. Here is an example of this site:
Preparing your attack
Here I see the undisputed master, I have named the one, the only, the great MetaSploit. This program, which can be used for free, allows exploiting payloads or to create one's own to exploit known flaws. An article about how to use the tool will soon arrive on this blog!
Be the least visible on the Internet
I think everybody expects it, but for me, I can hardly see being more effective than Tor at this point. Why Tor instead of VPN? Most VPN providers log your activity, and even if they sell you the fact that they don't, you can never be 100% sure.
As far as tor is concerned, there are some reliable alternatives for me:
- Tor browser: the official Tor browser based on Firefox.
- Brave: The privacy-oriented browser, which has a Tor mode (a solution I personally use)
Note that tor is automatically blocked on some sites, just like VPNs.
Analyzing network behavior
Analyzing the network behavior can also be a good approach, for that, the most adapted tool is, in my opinion, the TCPDump/WireShark combo. On Windows, you can use netsh or Microsoft powertools.
The interest in this kind of case can be to see with which server we communicate, which information we send and receive and according to which protocol.
Have a "toolbox" OS.

For the lazy (as I am), it is also possible to directly exploit an OS. I see two candidates here:
Kali Linux: The Debian-based OS is recognized in the cyber security community, the "by offensive security" model has nothing to prove. It has the advantage of having a big community of enthusiasts who feed it and put a lot of tutorials around it. For my part, it's my main Linux.
Parrot Linux: Distribution also based on Debian. This distribution has the same advantages as Kali, a ready-made packaging, a strong community. I just find that the community around the product is a bit less present (but that's just my point of view, I may be wrong).
Note that the two Linux mentioned above are about the same age. They were both released in 2013.
Attackers everywhere, what to do?
I've already said it several times during my missions, when I'm asked how to avoid being attacked, the answer is simple: it's impossible!
The Internet is a jungle, there's not much you can do about it.
The best solution remains surveillance and reactivity. You have to keep in mind that black hats will often remain discreet until they can launch their attacks, they can wait months before showing up. The goal in this case is to accumulate as much information as possible, or to infiltrate as far as possible into the information system.
Similarly, many attackers will not launch an attack at 3 Gb/second, which would only be of interest to be very visible.
So what do we do? Personally, I see three axes:
- Metrology and supervision: finely supervising a production infrastructure is essential, it allows us to detect abnormal behavior, the more information and hindsight we have, the easier it is to detect patterns that are out of the ordinary.
- Regularly auditing applications: at this point, I am not necessarily talking about using an external company to audit security, but rather about auditing the authorizations, the open flows of an application yourself. Is it still necessary for my application A to access application B? Does it need to have as much access, to see when the last uses were made, and so on?
- Test as much as possible: I already talked about it on this blog, DevSecOps must become the basis of your applications, testing security as soon as your application is developed is essential.
The most complicated will always remain to detect weak signals, i.e., discrete attacks. I have 2 examples in mind on this subject:
- A "brute force" attack on ADFS, via a botnet network, which made 5 attempts per minute, therefore lost in the "normal" flow of several hundreds or even thousands of connections over the same interval.
- A compromised machine that was infected by a cryptographer, who was mining Bitcoin using 10% of the CPU.
It is also possible to equip yourself accordingly. On AWS, the GuardDuty service does an excellent job of detecting this type of behavior.
As said earlier, a malicious attacker will always try to be as discreet as possible.

To pay the ransom or not?
Lately, a ransomware attack got a lot of attention. Garmin was indeed targeted by a cryptolocker and has been immobilized for over ten days. Looks like the company ultimately decided to pay the ransom.
$10,000,000 is the ransom price… Like the debit story, the amount is anecdotal for a company Garmin's size.
Still, from where I stand, paying ransom is always a bad idea:
We're talking about hackers, they have absolutely no obligation to unlock the data
If Garmin decided to pay today, what's to stop another company from doing so?
It is possible that another backdoor will be present in the system and lock again the company in a few months.
Paying encourages these attacks because it sends a signal that it's an effective way to make money.
To conclude this long article…
Rather than a conclusion as long as this article, I propose bullet points on the misconceptions about hacking:
- Hackers don't need 15 monitors and 8 computers…
- Hackers very rarely hack from mobile phones, at best it is used as an attack vector.
- Hacking a system is not done in a few seconds (except in very special cases), and sometimes takes several weeks or months.
- Social hacking is also a more and more common way to get in, as I have talked about it in the past.
- In movies and series, hacking is often used in Deus Ex Machina to avoid having to manage a too complicated story, computer science is often seen as an end and not a tool.
- Most of the movies and series that have hacking scenes often make me laugh (except Mr. Robot which is devilishly realistic).
- I don't dress in a hoodie to hack into systems
- Hackers are not all outcasts of the system and many go unnoticed, they just decided to play with their rules on the Internet.
If you want to train without risk (and without the risk of jail), I can only recommend the excellent hackthebox that will allow you to use your skills and sharpen your hacker talents. This site provides sandbox environments for hackers. Please note that you will need to "hack" the site in order to create an account.



Comments ()